A Glimpse at SEO Poisoning

During a recent investigation, I had the chance to dig into a case of SEO Poisoning. It’s a tactic that doesn’t get nearly enough attention, so I wanted to share what I found—especially how attackers choose domains and use SEO tricks to pull off these types of attacks.
What is SEO?
Search Engine Optimization (SEO) is a method web administrators use to improve how their webpages appear in search engine results like Google.
In essence, it’s about delivering a good user experience with fast, relevant results tailored to what someone is searching for.
A basic example is the use of keywords and tags that match what a user types into Google—for example, “dog adoption.” A well-optimized site will include that exact phrase and related terms, helping it rank higher.
If a page titled “Vacation Locations” showed up instead, it’d clearly be a poor match—bad SEO, and a bad user experience. Search engines are tuned to filter those kinds of irrelevant results.
SEO is a deep topic, but for now, the main takeaway is the importance of keywords—which we’ll come back to shortly.
What is SEO Poisoning?
SEO Poisoning is when attackers abuse SEO tactics to boost malicious websites in search engine rankings. The goal is to get their site to appear among the top results so unsuspecting users click it, thinking it’s legit.
These malicious pages often mimic the look and feel of the real site they’re impersonating, making the deception even more convincing.
Real World Example: DBeaver.io
In this case, the attackers cloned a popular free IT tool used for SQL database management - DBeaver.
Unfortunately, I couldn’t reproduce the malicious search result myself (Google’s algorithm is notoriously inconsistent and can vary by user/location), but based on triage artifacts and browser history, it was clear that SEO poisoning was used to lure the user into clicking the lookalike site.
So, here’s the question: Which site is legitimate?
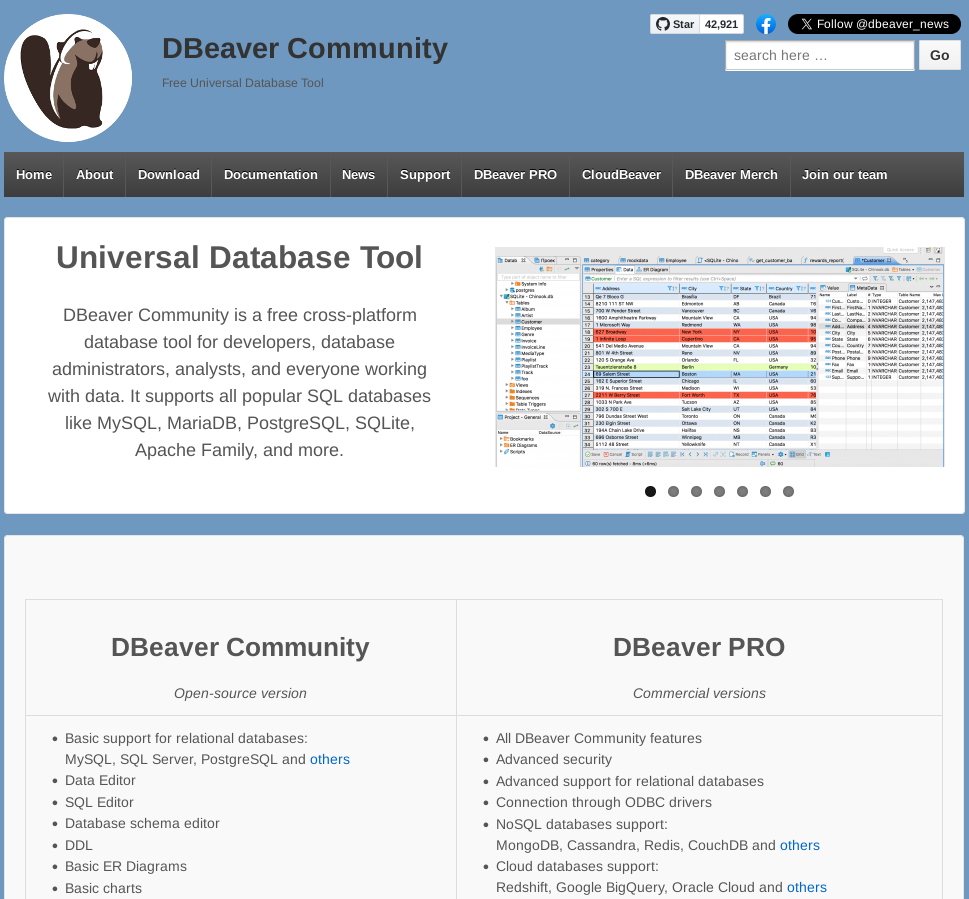
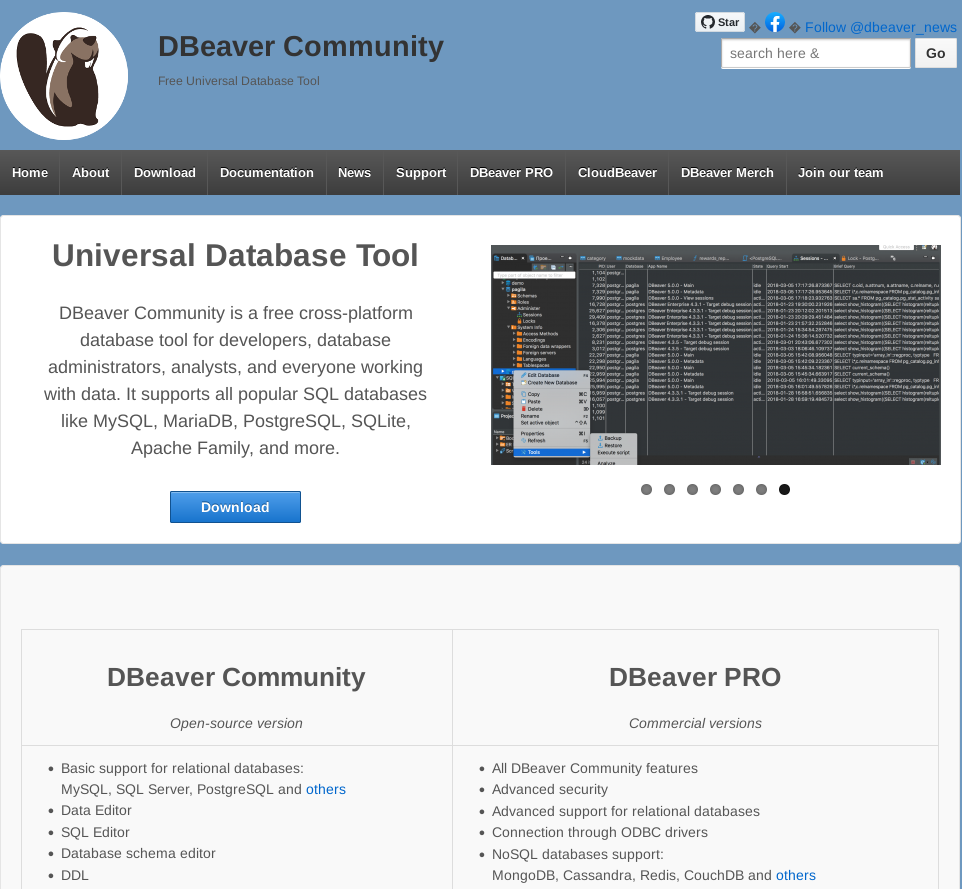
Comparison of legitimate and illegitimate DBeaver website.
The left image is of: https://dbeaver.io - The legitimate website for DBeaver
The right image is of: hxxps://dbeavercommunity[.]com - The malicious look-alike.
Minus the social icons in the top right, the only difference is the presence of the easily accessible 'Download' button on the right image.
Being mindful of links, I couldn't help but notice the download location takes you to a BitBucket repository: hxxps://bitbucket[.]org/masoniclabs/milajovovitch/downloads/
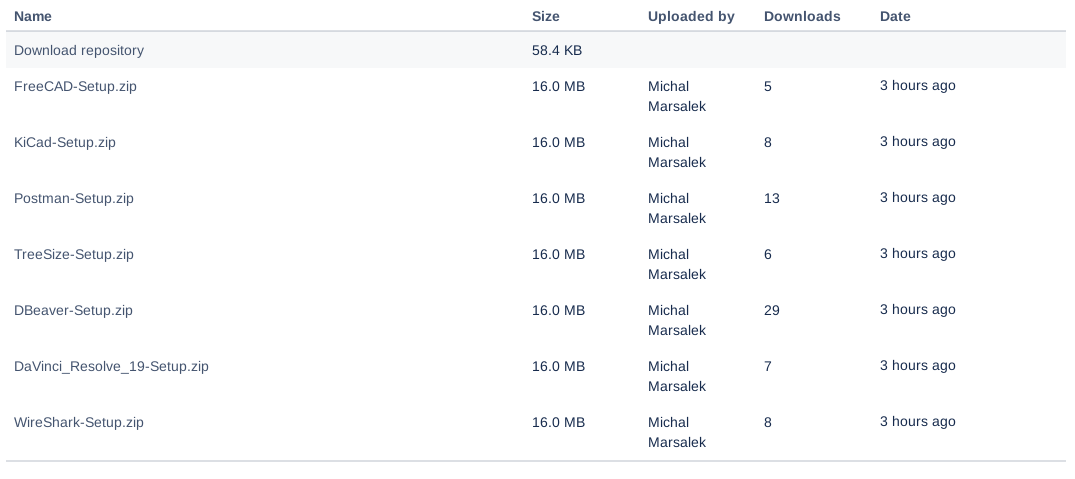
Whoa, this isn't just for DBeaver... it's for all of these other IT Tools as well. But we can see from the downloads that the DBeaver is the most popular by downloads thus far.
Naturally, as the good analyst I am, I threw the DBeaver-Setup.zip into a public sandbox to share: Hybrid Analysis
Certainly malicious, to no one's surprise, though I will not be going into depth on the malware analysis at this time, but will likely review in the future.
So how did this fake site get ranked high enough in Google search to trick a user?
How Attackers Choose Keywords
The success of SEO poisoning hinges on predicting what users are likely to search for—and this is exactly the kind of data attackers can gather just as easily as a marketing team would.
Coming from a background with Google AdWords certification, I’m familiar with the tools marketers use to analyze keyword performance and competitor strategy. And here's the kicker: attackers can and will use the same tools to plan their malicious campaigns.
We will be utilizing SpyFu, as you are able to perform a free report on a domain:
https://www.spyfu.com/overview/domain?query=https://dbeaver.io
This report allows us to see analytics for the legit DBeaver website such as keywords, clicks, and competitors.
Our two fields of interest are the 'Top Keywords' and 'Top Pages'
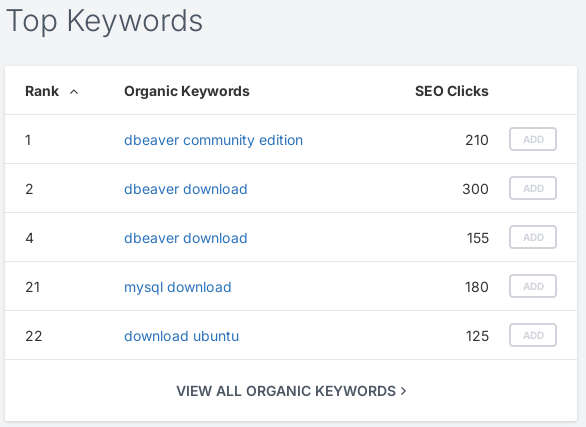
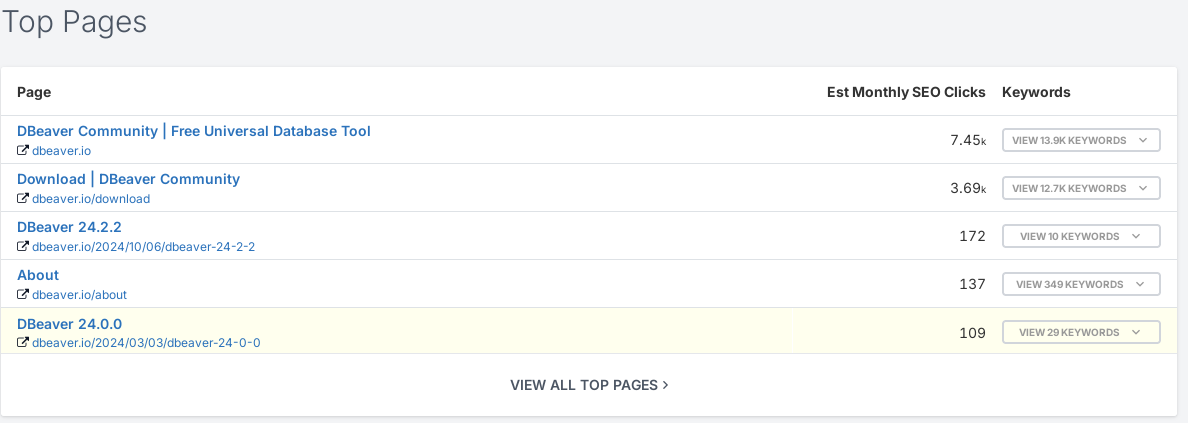
From the report, it’s clear that “dbeaver”, “community”, and “download” are high-value keywords. These are exactly the kinds of terms an attacker would target to get their fake site in front of the right audience—especially those in a hurry to install the tool.
And that’s exactly what happened in our example: hxxps://dbeavercommunity[.]com
The malicious domain blends a top keyword (“community”) with the tool’s name and mimics the real site’s layout. It’s a textbook example of how SEO poisoning exploits trust in search results—and it’s shockingly effective.
Why It Matters
SEO poisoning isn’t loud. It doesn’t crash systems or trigger flashy alerts. But it’s quietly one of the most effective ways to get a user to install malware—especially when the payload is disguised as a popular IT tool.
This tactic doesn’t just target casual users either. Developers, IT staff, and even security professionals are at risk—especially when trying to install tools quickly from search results.
What You Can Do
- Always verify domains manually. Don't trust that the top result is always legit.
- Use sandboxing or EDR solutions to catch malicious behavior post-execution.
- Report malicious domains to the hosting providers and reputation services, it'll proliferate.
- Utilize web proxy tools to block sites due to reputation or category (such as New Domain or Malware categories)
- Build a known-good software repository internally. Hosting vetted installers or official vendor links helps steer users away from these traps.
Final Thoughts
I got excited seeing something this fresh for once and I felt inclined to share insight into how you can exploit trusted platforms and SEO practices to deliver malware—without ever needing to touch a zero-day or deliver a phish. The tooling is simple, the sites are convincing, and the keywords are freely available for anyone to analyze.
Most users (even technically inclined ones) tend to trust what shows up at the top of a search result. That trust is exactly what SEO poisoning aims to exploit.
As defenders, it’s important we don’t just focus on network logs or EDR alerts—we also need to understand how users are finding the software they install in the first place and educate accordingly.
Thank you for reading,
~Austin




